In this post, I will discuss Security and the role it has within HFM applications. I will show how to change user access for different Security Classes, and also how to create a new user in an application. Both of these topics are very significant for assigning accessibility to your new HFM application.
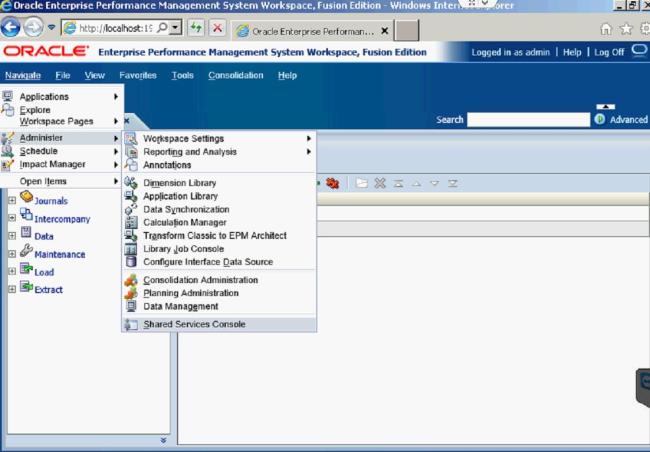
The Security Class within HFM is very important when setting up your new application. They allow you to specify who is allowed to see different things within the application. You can restrict which accounts someone has access to, which entities they can see, different scenarios they can look at, which Inter Company Partners they can see, and the access to different custom dimensions. After the Security Class has been associated with a certain dimension, you can assign the user privileges to those classes. This is done in Shared Services.
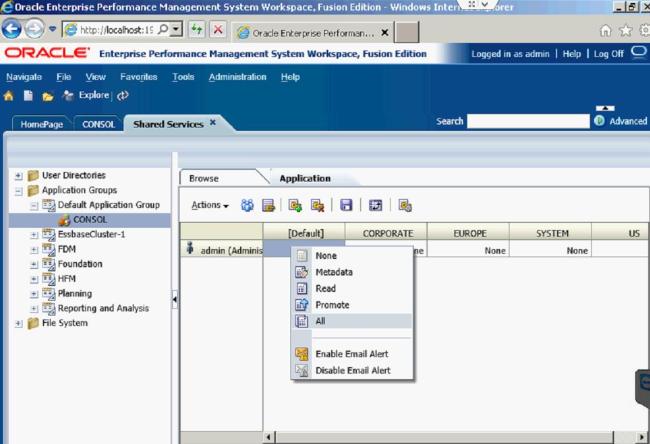
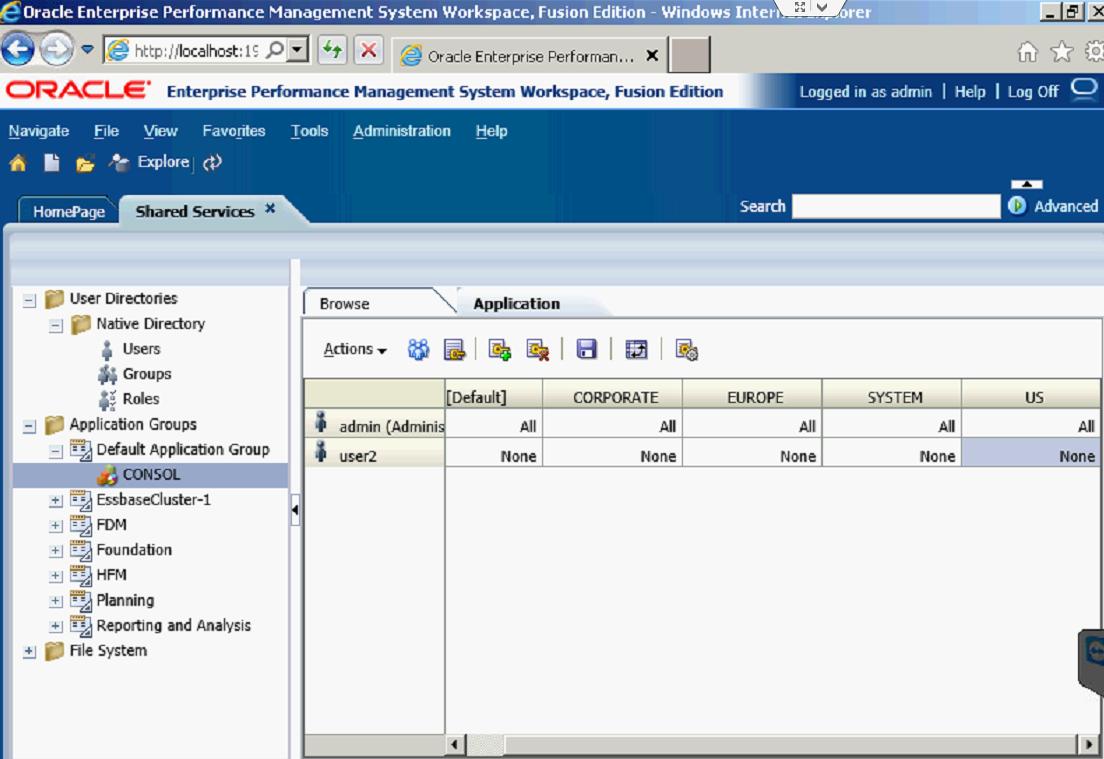
Once in Shared Services, you can assign access control for users and determine which access type users can have per security class.
The Default access type is None, meaning there is no security for that user with those Security Classes. There are five access types: None, Metadata, Read, Promote, and All.
Since I am the Administrator User, I have set the access for all the classes to All.
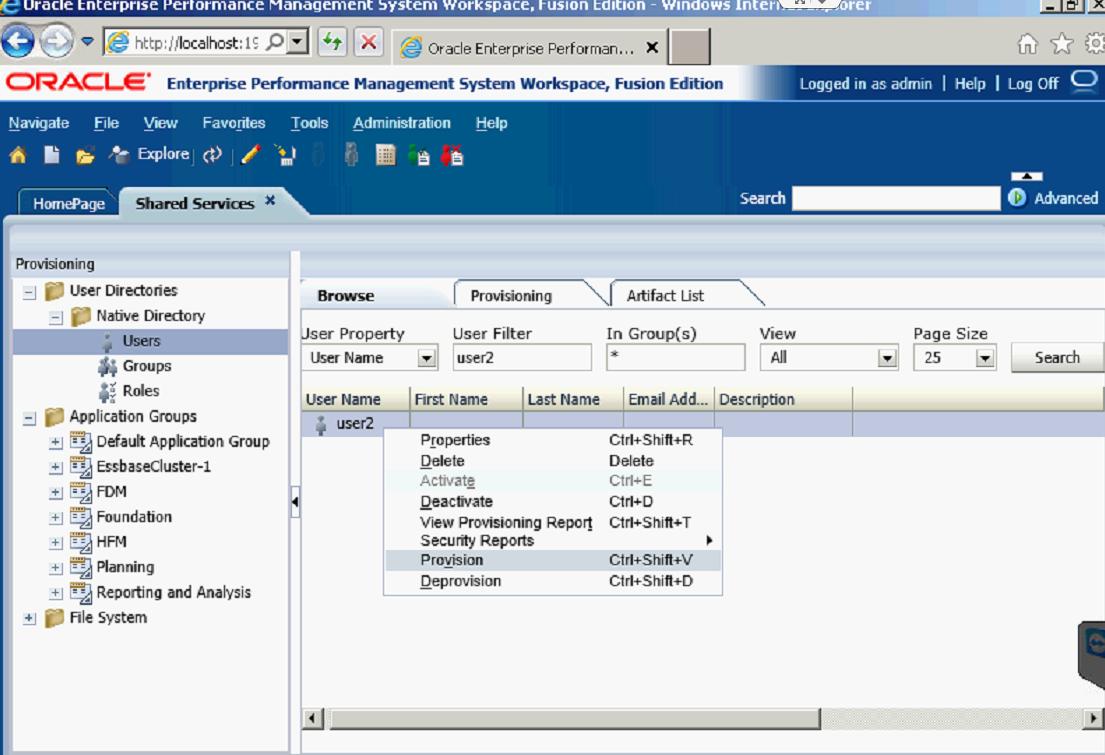
You can also create new users within the Shared Services Console. Right-click on User to pull up that option.
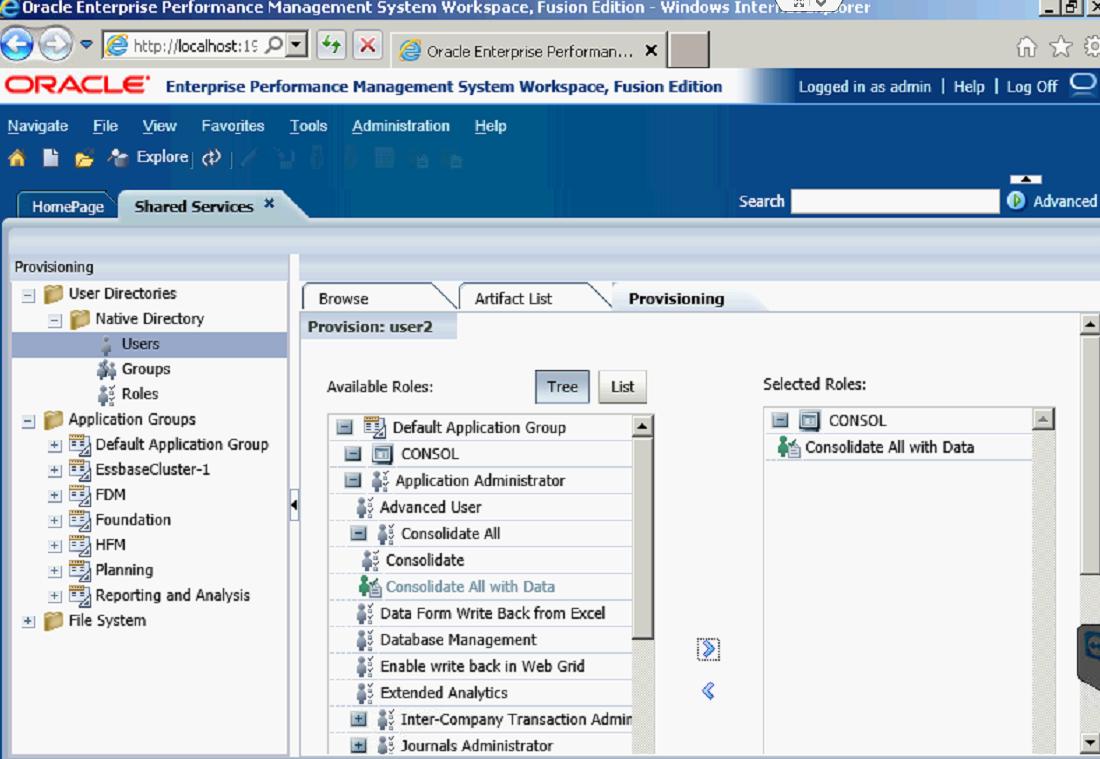
Once you have created the user, you need to assign it to an application. You do so by Right-clicking the user, and selecting Provisions.
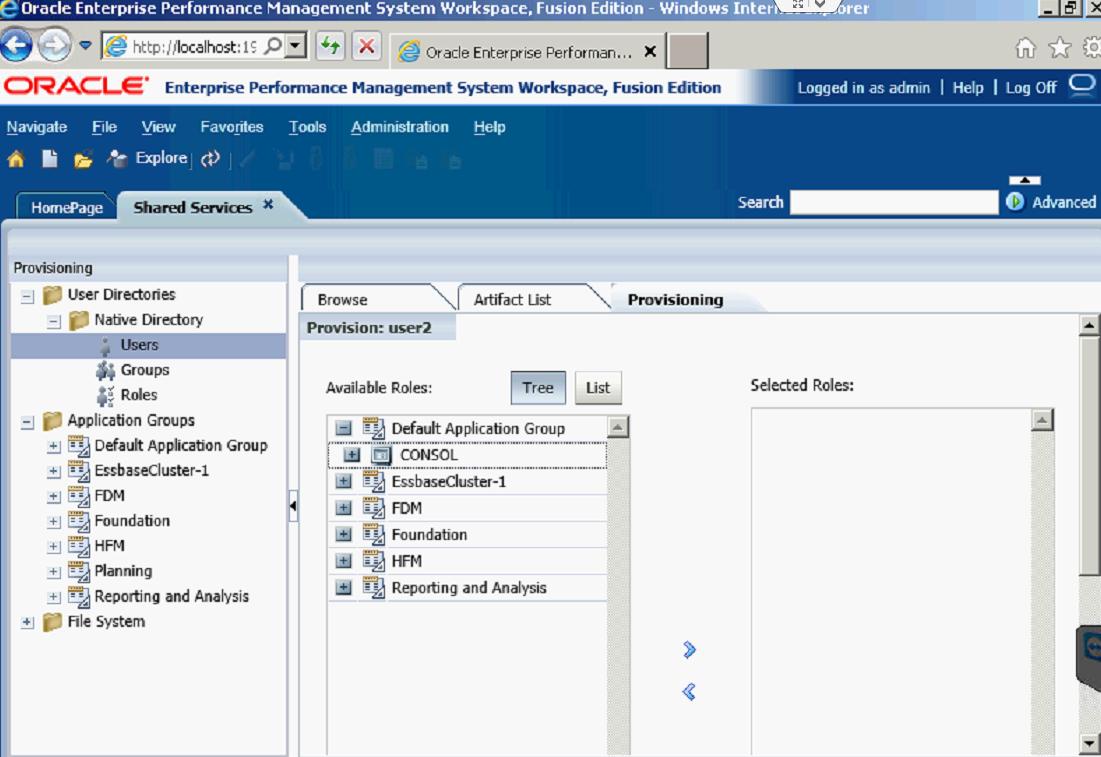
Then find and select the application you want to give the user access to.
After you find the application, you must give the user a role. The role I gave User2 was the Consolidate All with Data Role.
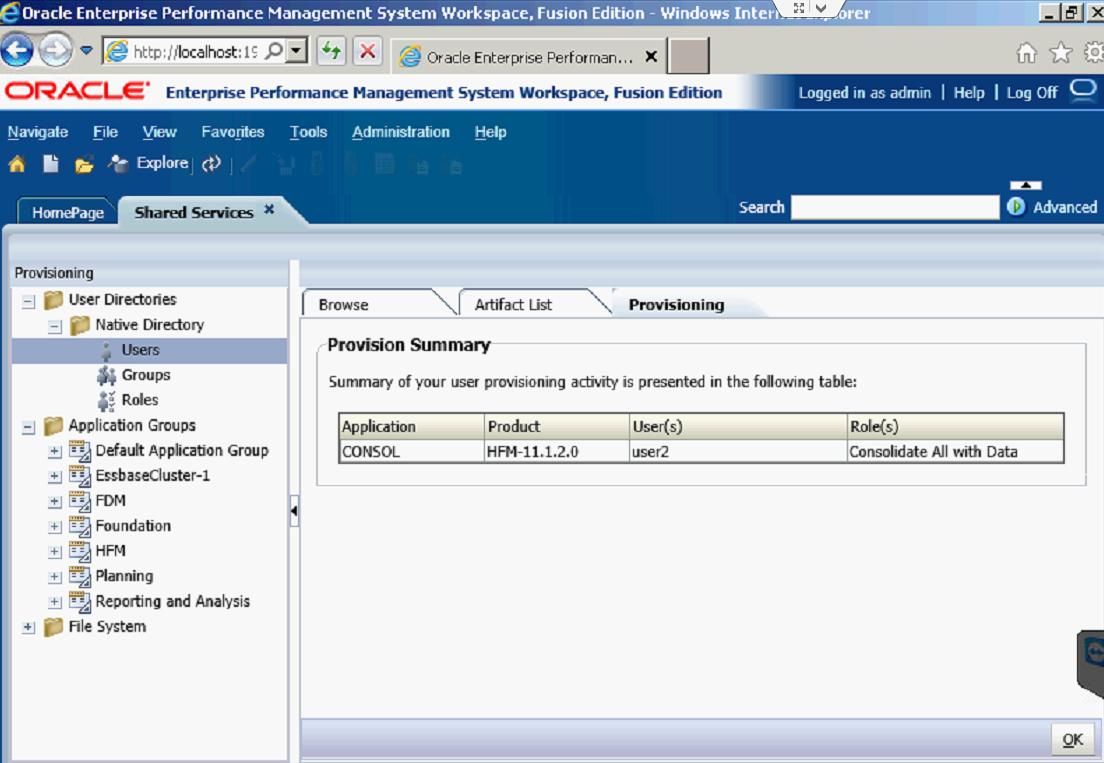
After you click OK, you will get a screen that tells you every role that has been assigned to that user.
From there, you can determine which access to give the new user in the existing Security Classes.
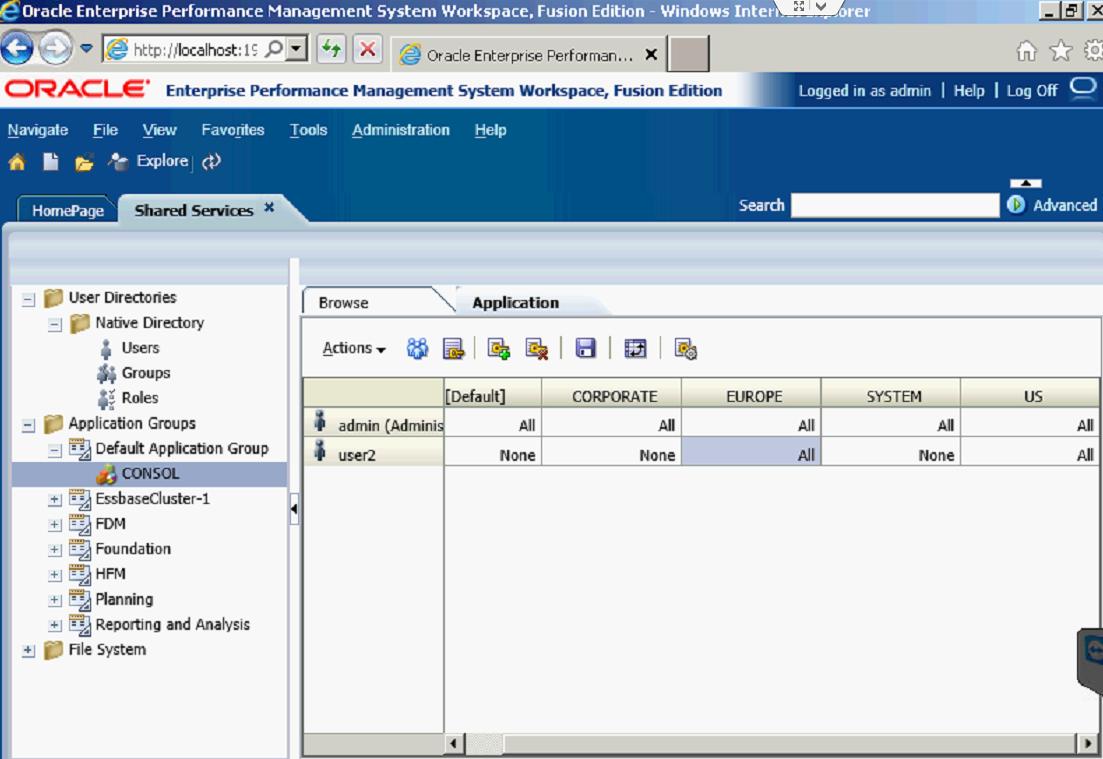
I gave User2 access to the US and EUROPE Security Classes.
Now User2 will only be able to run Consolidate All with Data in those two Security Classes.